Sponsored by Splunk
Sponsored by Sophos
IT Security & Attack Prevention
Sponsored by SAS Institute
Global AML Research: Acceleration Through Adversity
Sponsored by ReliaQuest
The Case for Open XDR-as-a-Service
Sponsored by MetricStream
State of IT and Cyber Risk Management Survey Report 2021
Sponsored by Exabeam
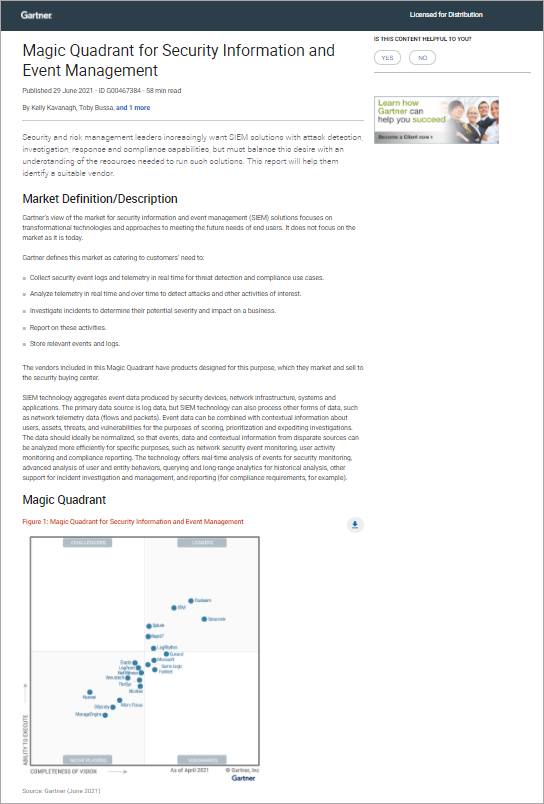
2021 Gartner Magic Quadrant for Security Information and Event Management (SIEM)
Sponsored by ServiceNow
Forrester TEI ServiceNow Security Operations Solutions
Sponsored by Sophos
How to Stay Protected Against Ransomware
Sponsored by Sophos
Checklist: How to Stop Ransomware in its Tracks
Sponsored by Sophos
The Future of Cybersecurity in Asia Pacific and Japan Report I Second Edition
Sponsored by Sophos
Sophos Plays a Quartet of Aces
Sponsored by Imperva
CISOs: Why Is Database Security So Elusive and What Can You Do About It?
Sponsored by Rapid7
Cybersecurity Best Practices for Business Resilience Series
Sponsored by Rapid7