Application Security , Card Not Present Fraud , Cybercrime as-a-service
IcedID Malware Revamped With Avoidance Capabilities
Banking Trojan Has Become More Prevalent Since COVID-19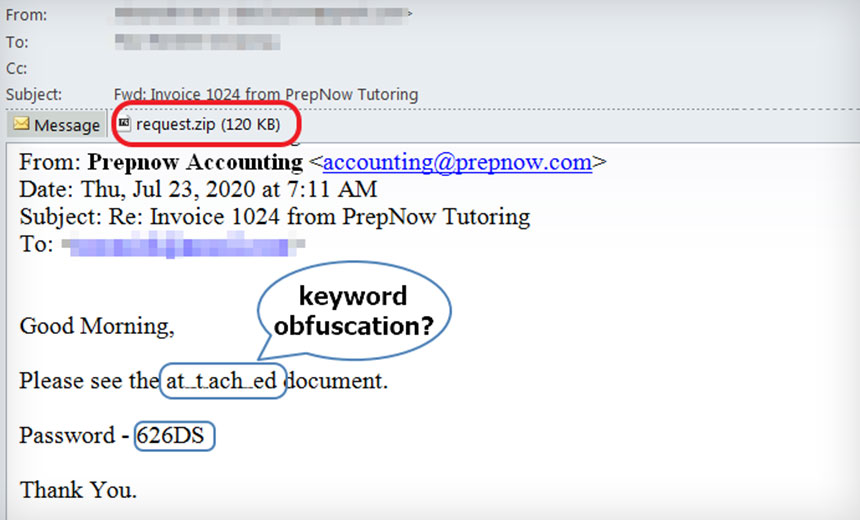
The IcedID banking Trojan has recently been updated with additional evasion techniques, including a password-protected attachment, keyword obfuscation and Dynamic Link Library file that acts as a second-stage downloader, according to Juniper Threat Labs.
See Also: The State of Organizations' Security Posture as of Q1 2018
The threat actors behind the campaign, first spotted in July, research their target before an attack to identify a handful of customer names, Juniper's new report states. Using a known name helps the hackers to entice the victim to open a phishing email that contains the Trojan, Paul Kimayong, a security researcher with Juniper Threat Labs, notes.
"This makes the phish that much more likely to succeed, given the sender and the recipient have an established business relationship," Kimayong says.
First observed in September 2017 by IBM X-Force researchers, IcedID steals financial data using malicious code injected into a web browser. The Trojan has been used more frequently since the COVID-19 pandemic started (see: Revamped IcedID Banking Trojan Campaign Uses COVID-19 Lure).
Evading Detection
The Juniper report finds that phishing emails are sent to potential victims from addresses that appear to originate with an accounting department and supposedly include an invoice. But the attachment actually is a malicious password-protected zip file.
The password protection is designed to prevent anti-malware tools from decrypting and inspecting the attachment. The password to the zip file is also included in the body of the email, Kimayong says.
The word "attached" in the message is also obfuscated in several ways. This is also an attempt for the phishing email to bypass spam filters or detection systems that search for specific keywords, Kimayong says. One example provided has the word "attached" spelled "At..t ach..ed."
Kimayong notes that this attempt at obfuscation "is useless because there is no need for any security solution to rely on the word 'attached' to figure out there is an attachment. If anything, we expected the obfuscation to obfuscate the word 'password' because that’s a tell-tale sign of something phishy going on."
In another possibly pointless maneuver, the researchers note that the campaign rotates the file name used for the attachment inside the zip file. Once again, the effectiveness is not clear.
"This seems futile, since the password protection should prevent most security solutions from opening and inspecting the content. Nonetheless, this technique proved successful against Google's Gmail security, which did not block this email," Kimayong notes.
Malicious Attachments
Once the zip file is extracted, the first stage of the attack launches. The file contains a malicious Word document that contains macros that the victim must enable for the malware to be downloaded, Kimayong says.
"There is the usual social engineering attempt to get victims to enable macros, which claims the document was created with a previous version of MS Word, in this case. Once macros are enabled, the VB script will download a [Dynamic Link Library file], save it as a PDF and install it as a service using regsvr32 to guarantee persistence," Kimayong says.
The second stage payload is a Dynamic Link Library file that is downloaded from either 3wuk8wv[.]com or 185.43.4[.]241 - websites that reside on a server in Russian, Kimayong says. Once downloaded, the malicious Dynamic Link Library file is saved as a PDF to maintain persistence in the infected device, the report notes.
"The second stage will download the third stage as a PNG file, decrypt it and run it. It will be saved as {random}.exe and will create a scheduled task for persistence. The third stage will download the IcedID main module as a PNG file, spawn a msiexec.exe process and inject the IcedID main module into it," Kimayong says
Third and final stage holds the payload downloader, according to the report.
"Similar to the second-stage loader we analyzed in our previous blog, this loader blends its traffic with requests to benign domains, such as apple.com, twitter.com, microsoft.com, etc. to look more benign to sandboxes trying to analyze it. Unfortunately, at the time of our testing, the download domain, loadhnichar[.]co for the next stage is already down," Kimayong notes.
Other Campaigns
Juniper found IcedID's operators have added steganography techniques - the practice of hiding malicious code in image files - according to a previous report.
Along with other phishing campaigns that are attempting to steal banking data and credentials, the IcedID Trojan is also being spread through COVID-19 phishing emails that include malicious attachments These attacks started in March and are ongoing (see: Revamped IcedID Banking Trojan Campaign Uses COVID-19 Lure).